Hackers managed to gain access to employee business emails, so they were able to capture the correspondence of clients and business partners of both companies. According to Niebezpiecznik, the attack took place at least a month ago. The clients of both companies who were concerned about malicious emails decided to inform the portal about such an incident.

Cleverly schemed phishing
Cybercriminals sent messages to their victims with infected attachments included that contained the Trojan Emotet (malspam). The program can grant itself access to the victim’s electronic banking and equally may capture files from the victim’s device and encrypt them. In such a case, all the victim has to do is open the attachment that will install the software. The possibility of the attack’s success was very high because hackers impersonated company employees by using their e-mail aliases. Then they copied fragments from previous correspondences and pasted them into their infected messages, which significantly confirmed their “authenticity”:
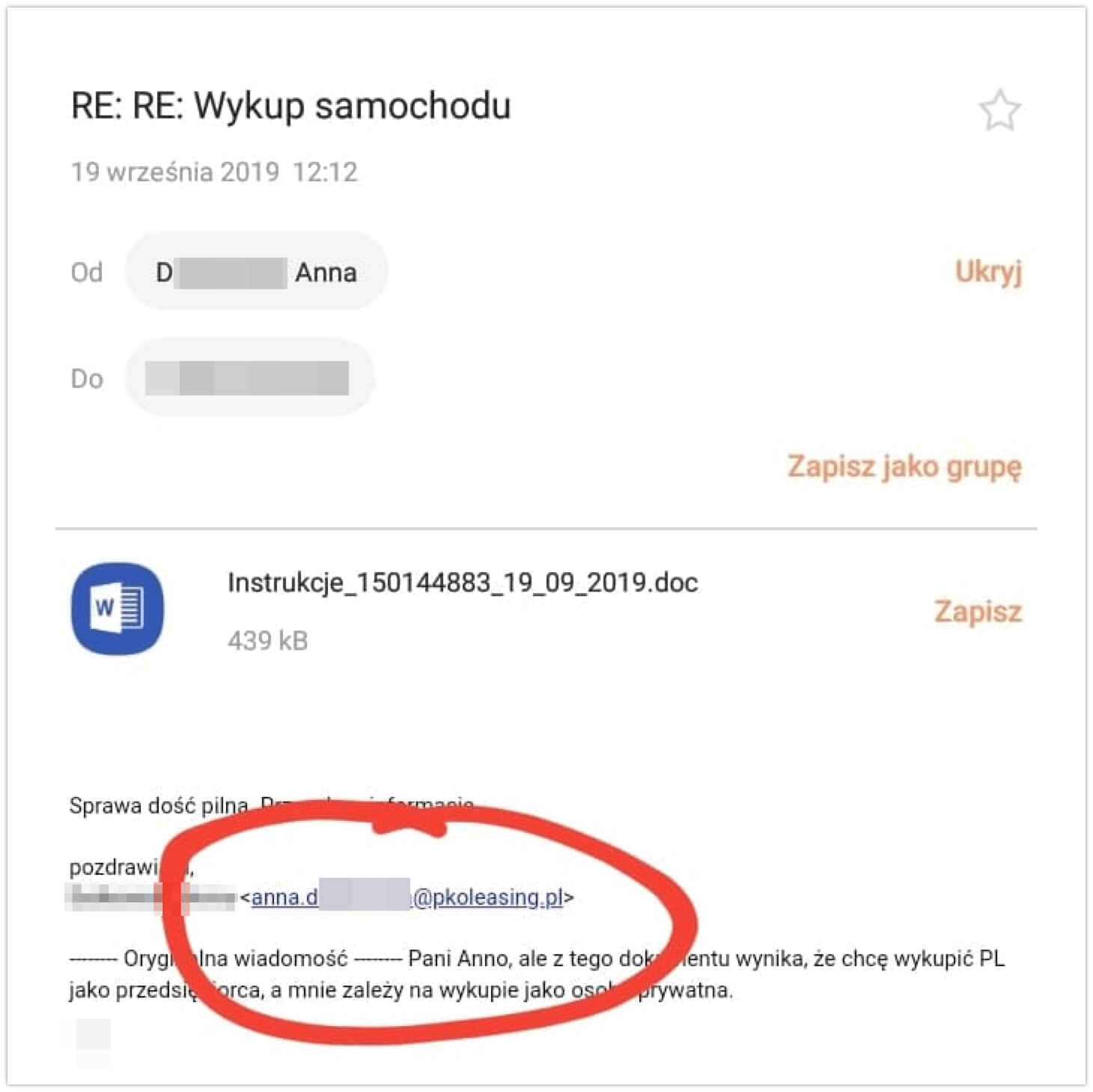
The Niebezpiecznik albo notes, that the names of the attachments themselves looked very authentic:
- Instructions_150144883_19_09_2019.doc
- Agreement_project 0391310451 23 09 2019.doc
- Scanned_documents_9543481_24_09_2019.doc
So far, we do not how large the scale of these attacks is, but the matter does not look good. As an outcome of the cyber attack, not only confidential correspondence of clients/business partners and institutions’ employees fell into hackers’ hands but most of all, users’ devices and bank account were exposed to cybercriminals.
Both companies have already informed their customers about the data leak and, as they say, try to address the issue. According to the editors of the portal Niebezpiecznik, it was probably about phishing, which firstly tricked employees. And this enabled cybercriminals to take further action.
See also: „Zapłać albo opublikujemy twoje kompromitujące wideo”. Oszust rozsyła maile z pogróżkami
DB
Source: niebezpiecznik.pl



